Risk Scenarios
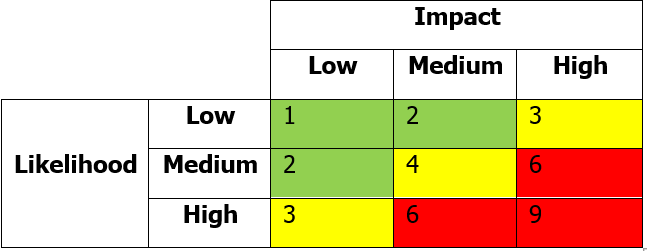
As a baseline for identifying and assessing cyber risks, a risk scenario approach can be used. For that reason, a predefined risk register and assessment tool has been created to ease the cyber risk identification and assessment process. As a first task, an organization should analyse the list of threats and risk scenarios that is listed in Annex 1. During this task, all irrelevant risk scenarios and threats should be removed. The rest of them can be modified to reflect the current cyber risk landscape where the organization is operating. Next, additional risk scenarios along with accompanying threats should be described in the risk register. Once the list of threats and risk scenarios is analysed and fine-tuned according to the specifics of the organization and the environment, an assessment of risk scenario impact and likelihood should take place. The scales of impact and likelihood can be customized according to the specifics of the organization. One of the most lightweight scaling would describe likelihood and impact as follows:

![]() An assessment of risk scenario impact and likelihood gives the organization an overview of the most critical risk scenarios. When advancing to the next step of risk treatment, those controls that treat the most critical risks should be applied as the first priority.
An assessment of risk scenario impact and likelihood gives the organization an overview of the most critical risk scenarios. When advancing to the next step of risk treatment, those controls that treat the most critical risks should be applied as the first priority.
Risk Assessment
After the value of the information assets is determined, a more advanced approach can be used instead of risk scenarios to assess the information security risks. This step of risk assessment identifies the applicable threats and vulnerabilities that exist, determines the potential consequences and, finally, prioritizes the derived risks.

Figure 2: Risk management process according to ISO/IEC 27005:2018.
Risk identification
The purpose of risk identification is to determine what can happen to cause a potential loss, and to gain insight into how, where and why the loss can happen. Risk identification requires input from identification of threats, existing controls, vulnerabilities and consequences.
Identification of threats
A threat has the potential to harm assets such as information, processes and systems and, therefore, organizations. Threats can be of natural or human origin, and can be accidental or deliberate. Both accidental and deliberate threat sources should be identified. A threat can arise from within or from outside the organization.
Input to the threat identification can be obtained from the asset owners or users, human resources staff, facility management and information security specialists, physical security experts, legal department, the CERT, and other relevant organizations. Internal experience from incidents and past threat assessments should be considered in the current assessment.
Identification of existing controls
Identification of existing controls should be made to avoid unnecessary work or cost, e.g. in the duplication of controls. In addition, while identifying the existing controls, a check should be made to ensure that the controls are working correctly.
An existing control can be identified as ineffective, or insufficient, or not justified. If not justified or insufficient, the control should be checked to determine whether it should be removed, replaced by another more suitable control, or whether it should stay in place, for example, for cost reasons.
Identification of vulnerabilities
Vulnerabilities can be identified in the areas of organization, processes, management routines, personnel, environment, system configuration or equipment. The presence of a vulnerability does not cause harm in itself, as there needs to be a threat exploiting it. A vulnerability that has no corresponding threat may not require the implementation of a control, but should be recognized and monitored for changes.
Identification of consequences
A consequence can be loss of effectiveness, adverse operating conditions, loss of business, reputation, or damage. This activity identifies the damage or consequences to the organization that can be caused by an incident scenario. An incident scenario is the description of a threat exploiting a certain vulnerability or set of vulnerabilities in an information security incident.
Risk Analysis
Assessment of consequences
Firstly, the business impact on the organization that can result from possible or actual information security incidents should be assessed, taking into account the consequences of a breach of information security such as loss of confidentiality, integrity or availability of the assets. To measure the consequences, the business impact value can be expressed in qualitative and quantitative forms, but any method of assigning monetary value can generally provide more information for decision making.
Assessment of incident likelihood
After identifying the incident scenarios, it is necessary to assess the likelihood and impact of each scenario. This should take account of how often the threats occur and how easily the vulnerabilities can be exploited.
Level of risk determination
Risk analysis assigns values to the likelihood and the consequences of a risk. Risk analysis is based on assessed consequences and likelihood. Additionally, it can consider cost-benefit, the concerns of stakeholders, and other variables, as appropriate for risk evaluation. The estimated risk is a multiplication of the likelihood of an incident scenario and its consequences.

Risk Evaluation
In this step, the level of risk is compared against the risk evaluation criteria and the risk acceptance criteria. Decisions that are taken in the risk evaluation activity are mainly based on the acceptable level of risk. The following are an example of risk acceptance criteria:
a) The impact is low
b) The cost of treatment is not cost-effective (more expensive than not applying the treatment) and its implementation is lengthy (takes months or more) c) The risk can be tolerated in a short-term perspective (in a case-by-case basis, e.g. for less than 72 hours, less than 5 days…).
However, these examples are not exhaustive and an organization may decide to accept certain risks due to its specific context.
Also consequences, likelihood, and the degree of confidence in the risk identification and analysis should be considered for risk evaluation. Risk evaluation uses the understanding of risk obtained by risk analysis to take decisions about future actions. Decisions should include:
a) whether an activity should be undertaken
b) priorities for risk treatment considering estimated levels of risks.
For example, it is mandatory to treat risks with the medium and high risk level and it is optional but recommended to treat risks with a low risk level. The higher the risk level, the more urgent the risk treatment activity is. The risk treatment activity most often resuls in applying new or amending the existing security controls, which lower the likelihood and/or impact of the cyber risk. Risk evaluation, and especially risk acceptance, must be always subject to management’s approval.